PORTA27
Display

(HP-41CX, Hewlett Packard 1983 and DM41X, SwissMicros 2020)
Overview
Program PORTA 27 implements an encryption variation by Giambattista della Porta, known as polyalphabetic cipher, so called bigraphic substitution. Porta published De Furtivis Literarum Notis in 1563. This program is written for the HP-41CX as minimisation of the program in chapter 7 of the book: Kryptologie (HP-41 C/CV): Chiffrierung, Textverschlüsselung, Datenschutz, Morsealphabet; Alt, Helmut; Schumny, Harald [Hrsg.], Braunschweig [u.a.]. Vieweg. 1983. Vieweg-Programm-bibliothek Taschenrechner Band 7. ISBN 3-528-04256-7.
Formula
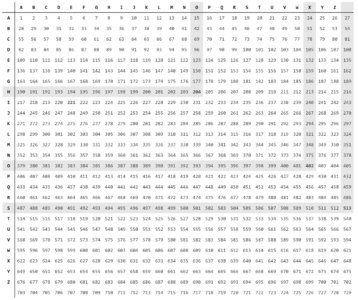
Coding according to Porta is done by looking up the value of two consecutive characters in a table (see Encryption Table). For example the word “PO” can be coded as 420. If a word has an odd number of characters, a space is appended for completion of the Porta coding. The table lookup can be computed by following below algorithms:
| FORWARD | Taking the two consecutive characters in a word C1 and C2, the Porta code cp can be determined as follows: | |
| cp = 27.(C1 – 1) + C2 | C1, C2 are A..Z,space | |
| cp = 27.C1 + C2 – 1819 | Substituting Ci = Ci + (65-1), where 65 is char value of A | |
| BACKWARD | Taking the Porta code cp, the two consecutive characters in a word C1 and C2 can be determined as follows: | |
|
C1 = INT(0,99 + cp/27) C2 = INT(0,99 + 27.FRC(cp/27)) |
cp is 1..729 | |
The lookup table shows a base of 27. More bases are possible if more characters need to be encrypted. An example of coding the word HOOXIES is given in the encryption table which translates the word into a series of cp values: 204, 402, 221 and 513.
Encryption Table
Cross first character in the left column with the second character in the top row. The character sequence is the encrypted code.
For example, the word HOOXIES can be coded as follows:
1. "HO", in table is: 204
2. "OX", in table is: 402
3. "IE", in table is: 221
4. "S ", in table is: 513
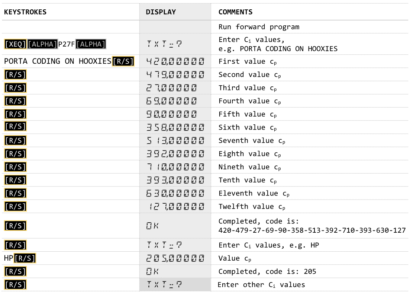
Example (1)
Please note my default FIX 5 setting in de examples below for the codes.
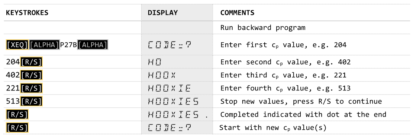
Example (2)
Below example decrypts a numerical sequence back to a text.
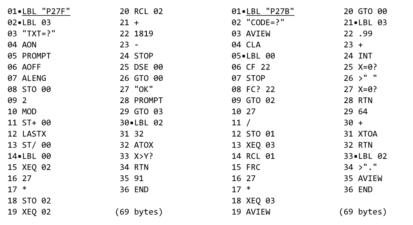
Program Listing
P27F makes use of an optimised (forward) algorithm that includes the character values of alphas A..Z (65..90). However, the space value (32) does not fit so nicely in this sequence, the formulae is non-linear. In LBL 02 this is intercepted by checking against 32. If the
ATOX value exceeds 32, it can proceed according to the forward algorithm, otherwise it substitutes the value 91 representing the character value of a space in the optimised (forward) algorithm.
P27B has to cope with the same non-linear problem of the space. In
LBL 03 it checks whether the calculated character value is zero. This happens for character 27 (space) and results in cp/27 getting very close to zero. The program checks whether X=0? and appends a space to the text string, otherwise it converts XTOA (atter first adding 64 to any of the possible values 1..26).
Downloads
PDF format of programs P27F and P27B.
RAW/TXT format of programs P27F and P27B (in zip file).
© 2009-2020 by Auke Hoekstra





























 2017
2017 2020
2020 2020
2020 2013
2013 2011
2011 2014
2014 2016
2016 2018
2018 2010
2010 2022
2022 2019
2019 2013
2013 2014
2014 2019
2019 2018
2018 2023
2023 2016
2016 2015
2015 2019
2019 2023
2023 2013
2013 2023
2023